Authentication, Authorization, and Identity with Vault
Overview
Authentication in Vault is the process by which user or machine supplied information is verified against an internal or external system. Vault supports multiple auth methods including GitHub, LDAP, AppRole, and more.
Identity is used to maintain the clients who are recognized by Vault. As such, Vault provides an identity management solution through the Identity secrets engine. In this lab, you will learn about the different types of authentication and auth methods, as well as how to interact with identity in Vault.
Task 1. Install Vault
Welcome to Cloud Shell! Type "help" to get started.
Your Cloud Platform project in this session is set to qwiklabs-gcp-02-e8fc74852051.
Use “gcloud config set project [PROJECT_ID]” to change to a different project.
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
Warning: apt-key is deprecated. Manage keyring files in trusted.gpg.d instead (see apt-key(8)).
OK
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ sudo apt-get update
sudo apt-get install vault
********************************************************************************
You are running apt-get inside of Cloud Shell. Note that your Cloud Shell
machine is ephemeral and no system-wide change will persist beyond session end.
To suppress this warning, create an empty ~/.cloudshell/no-apt-get-warning file.
The command will automatically proceed in 5 seconds or on any key.
Visit https://cloud.google.com/shell/help for more information.
********************************************************************************
Ign:1 https://us-apt.pkg.dev/projects/demosite-images demosite-apt InRelease
Get:2 https://repo.mysql.com/apt/debian bullseye InRelease [12.9 kB]
Get:3 https://cli.github.com/packages bullseye InRelease [3,921 B]
Get:4 https://download.docker.com/linux/debian bullseye InRelease [43.3 kB]
Get:5 https://packages.microsoft.com/debian/11/prod bullseye InRelease [3,629 B]
Ign:6 https://ftp.debian.org/debian stretch InRelease
Get:7 https://deb.debian.org/debian bullseye InRelease [116 kB]
Get:8 https://deb.debian.org/debian bullseye-updates InRelease [44.1 kB]
Get:9 https://deb.debian.org/debian-security bullseye-security InRelease [48.4 kB]
Ign:10 https://ftp.debian.org/debian stretch-backports InRelease
Ign:11 https://ftp.debian.org/debian stretch-updates InRelease
Err:12 https://ftp.debian.org/debian stretch Release
404 Not Found [IP: 199.232.46.132 443]
Get:13 https://cli.github.com/packages bullseye/main amd64 Packages [344 B]
Get:14 https://download.docker.com/linux/debian bullseye/stable amd64 Packages [25.2 kB]
Err:15 https://ftp.debian.org/debian stretch-backports Release
404 Not Found [IP: 199.232.46.132 443]
Err:16 https://ftp.debian.org/debian stretch-updates Release
404 Not Found [IP: 199.232.46.132 443]
Get:17 https://packages.microsoft.com/debian/11/prod bullseye/main amd64 Packages [83.3 kB]
Get:18 https://packages.microsoft.com/debian/11/prod bullseye/main arm64 Packages [14.6 kB]
Get:19 https://packages.microsoft.com/debian/11/prod bullseye/main armhf Packages [13.4 kB]
Get:20 https://deb.debian.org/debian bullseye/main Sources [11.4 MB]
Get:21 https://deb.debian.org/debian bullseye/main amd64 Packages [11.1 MB]
Hit:22 https://apt.llvm.org/bullseye llvm-toolchain-bullseye-13 InRelease
Get:23 https://storage.googleapis.com/bazel-apt stable InRelease [2,256 B]
Get:24 https://deb.debian.org/debian-security bullseye-security/main Sources [302 kB]
Get:25 https://deb.debian.org/debian-security bullseye-security/main amd64 Packages [300 kB]
Get:26 https://apt.postgresql.org/pub/repos/apt bullseye-pgdg InRelease [116 kB]
Get:27 https://storage.googleapis.com/bazel-apt stable/jdk1.8 amd64 Packages [9,940 B]
Get:28 https://packages.sury.org/php bullseye InRelease [6,841 B]
Get:29 https://repo.mysql.com/apt/debian bullseye/mysql-8.0 Sources [950 B]
Get:30 https://repo.mysql.com/apt/debian bullseye/mysql-8.0 amd64 Packages [8,596 B]
Get:31 https://repo.mysql.com/apt/debian bullseye/mysql-tools amd64 Packages [7,932 B]
Get:32 https://apt.postgresql.org/pub/repos/apt bullseye-pgdg/main amd64 Packages [445 kB]
Get:33 https://packages.sury.org/php bullseye/main amd64 Packages [376 kB]
Get:34 https://packages.cloud.google.com/apt apt-transport-artifact-registry-stable InRelease [5,094 B]
Get:35 https://packages.cloud.google.com/apt gcsfuse-stretch InRelease [5,006 B]
Get:36 https://packages.cloud.google.com/apt cloud-sdk-bullseye InRelease [6,400 B]
Get:37 https://apt.releases.hashicorp.com bullseye InRelease [12.9 kB]
Get:38 https://packages.cloud.google.com/apt gcsfuse-stretch/main amd64 Packages [2,217 B]
Get:39 https://packages.cloud.google.com/apt cloud-sdk-bullseye/main amd64 Packages [280 kB]
Get:40 https://apt.releases.hashicorp.com bullseye/main amd64 Packages [102 kB]
Get:1 https://us-apt.pkg.dev/projects/demosite-images demosite-apt InRelease [1,094 B]
Get:41 https://us-apt.pkg.dev/projects/demosite-images demosite-apt/main amd64 Packages [41.3 kB]
Reading package lists... Done
E: The repository 'https://ftp.debian.org/debian stretch Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
E: The repository 'https://ftp.debian.org/debian stretch-backports Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
E: The repository 'https://ftp.debian.org/debian stretch-updates Release' no longer has a Release file.
N: Updating from such a repository can't be done securely, and is therefore disabled by default.
N: See apt-secure(8) manpage for repository creation and user configuration details.
N: Repository 'https://deb.debian.org/debian bullseye InRelease' changed its 'Version' value from '11.6' to '11.7'
********************************************************************************
You are running apt-get inside of Cloud Shell. Note that your Cloud Shell
machine is ephemeral and no system-wide change will persist beyond session end.
To suppress this warning, create an empty ~/.cloudshell/no-apt-get-warning file.
The command will automatically proceed in 5 seconds or on any key.
Visit https://cloud.google.com/shell/help for more information.
********************************************************************************
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following NEW packages will be installed:
vault
0 upgraded, 1 newly installed, 0 to remove and 78 not upgraded.
Need to get 51.8 MB of archives.
After this operation, 179 MB of additional disk space will be used.
Get:1 https://apt.releases.hashicorp.com bullseye/main amd64 vault amd64 1.13.2-1 [51.8 MB]
Fetched 51.8 MB in 1s (36.9 MB/s)
debconf: delaying package configuration, since apt-utils is not installed
Selecting previously unselected package vault.
(Reading database ... 142190 files and directories currently installed.)
Preparing to unpack .../vault_1.13.2-1_amd64.deb ...
Unpacking vault (1.13.2-1) ...
Setting up vault (1.13.2-1) ...
Generating Vault TLS key and self-signed certificate...
Generating a RSA private key
..............................................................++++
............++++
writing new private key to 'tls.key'
-----
Vault TLS key and self-signed certificate have been generated in '/opt/vault/tls'.
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault
Usage: vault <command> [args]
Common commands:
read Read data and retrieves secrets
write Write data, configuration, and secrets
delete Delete secrets and configuration
list List data or secrets
login Authenticate locally
agent Start a Vault agent
server Start a Vault server
status Print seal and HA status
unwrap Unwrap a wrapped secret
Other commands:
audit Interact with audit devices
auth Interact with auth methods
debug Runs the debug command
events
kv Interact with Vault's Key-Value storage
lease Interact with leases
monitor Stream log messages from a Vault server
namespace Interact with namespaces
operator Perform operator-specific tasks
patch Patch data, configuration, and secrets
path-help Retrieve API help for paths
pki Interact with Vault's PKI Secrets Engine
plugin Interact with Vault plugins and catalog
policy Interact with policies
print Prints runtime configurations
secrets Interact with secrets engines
ssh Initiate an SSH session
token Interact with tokens
transit Interact with Vault's Transit Secrets Engine
version-history Prints the version history of the target Vault server
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
Task 2. Start the Vault server
With Vault installed, the next step is to start a Vault server.
Vault operates as a client/server application. The Vault server is the only piece of the Vault architecture that interacts with the data storage and backends. All operations done via the Vault CLI interact with the server over a TLS connection.
In this lab, you will start and interact with the Vault server running in development mode.
This dev-mode server requires no further setup, and your local vault CLI will be authenticated to talk to it. This makes it easy to experiment with Vault or start a Vault instance for development. Every feature of Vault is available in “dev” mode. The -dev flag just short-circuits a lot of setup to insecure defaults.
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault server -dev
==> Vault server configuration:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: ACTIVE_CUSTOM_IMAGE, API_DOGFOOD, ASPNETCORE_URLS, BASHRC_GOOGLE_PATH, BASHRC_PATH, BROWSER, CLOUDSDK_CONFIG, CLOUDSDK_DIAGNOSTICS_HIDDEN_PROPERTY_ALLOWLIST, CLOUDSDK_DIAGNOSTICS_HIDDEN_PROPERTY_WHITELIST, CLOUDSDK_PYTHON, CLOUDSHELL_ENVIRONMENT, CLOUDSHELL_OPEN_DIR, CLOUD_SHELL, CLOUD_SHELL_IMAGE_VERSION, CREDENTIALS_SERVICE_PORT, CUSTOM_ENVIRONMENT, DEVSHELL_CLIENTS_DIR, DEVSHELL_GCLOUD_CONFIG, DEVSHELL_IP_ADDRESS, DEVSHELL_PROJECT_ID, DEVSHELL_SERVER_URL, DOCKER_HOST, DOTNET_SKIP_FIRST_TIME_EXPERIENCE, GCE_METADATA_HOST, GEM_HOME, GEM_PATH, GODEBUG, GOOGLE_CLOUD_PROJECT, GOOGLE_CLOUD_QUOTA_PROJECT, GOOGLE_CLOUD_SHELL, GOPATH, HISTFILESIZE, HISTSIZE, HOME, JAVA_HOME, LANG, LOGNAME, LS_COLORS, MINIKUBE_FORCE_SYSTEMD, MINIKUBE_HOME, MINIKUBE_WANTUPDATENOTIFICATION, PATH, PROMPT_COMMAND, PS1, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, TMUX, TMUX_PANE, TRUSTED_ENVIRONMENT, USER, USER_EMAIL, USE_CLOUD_SDK_PYTHON3, USE_GKE_GCLOUD_AUTH_PLUGIN, V2V_GCP_V2V_IMAGE, WEB_HOST, _, __TMP_CLOUDSDK_CONFIG
Go Version: go1.20.3
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.13.2, built 2023-04-25T13:02:50Z
Version Sha: b9b773f1628260423e6cc9745531fd903cae853f
==> Vault server started! Log data will stream in below:
2023-05-01T03:30:56.175Z [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-05-01T03:30:56.175Z [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set
2023-05-01T03:30:56.176Z [INFO] core: Initializing version history cache for core
2023-05-01T03:30:56.176Z [INFO] core: security barrier not initialized
2023-05-01T03:30:56.176Z [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1
2023-05-01T03:30:56.177Z [INFO] core: post-unseal setup starting
2023-05-01T03:30:56.202Z [INFO] core: loaded wrapping token key
2023-05-01T03:30:56.202Z [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-05-01T03:30:56.202Z [INFO] core: no mounts; adding default mount table
2023-05-01T03:30:56.203Z [INFO] core: successfully mounted: type=cubbyhole version="v1.13.2+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-05-01T03:30:56.203Z [INFO] core: successfully mounted: type=system version="v1.13.2+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-05-01T03:30:56.203Z [INFO] core: successfully mounted: type=identity version="v1.13.2+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-05-01T03:30:56.204Z [INFO] core: successfully mounted: type=token version="v1.13.2+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-05-01T03:30:56.205Z [INFO] rollback: starting rollback manager
2023-05-01T03:30:56.205Z [INFO] core: restoring leases
2023-05-01T03:30:56.206Z [INFO] expiration: lease restore complete
2023-05-01T03:30:56.208Z [INFO] identity: entities restored
2023-05-01T03:30:56.208Z [INFO] identity: groups restored
2023-05-01T03:30:56.209Z [INFO] core: Recorded vault version: vault version=1.13.2 upgrade time="2023-05-01 03:30:56.208972778 +0000 UTC" build date=2023-04-25T13:02:50Z
2023-05-01T03:30:56.438Z [INFO] core: post-unseal setup complete
2023-05-01T03:30:56.438Z [INFO] core: root token generated
2023-05-01T03:30:56.438Z [INFO] core: pre-seal teardown starting
2023-05-01T03:30:56.438Z [INFO] rollback: stopping rollback manager
2023-05-01T03:30:56.438Z [INFO] core: pre-seal teardown complete
2023-05-01T03:30:56.439Z [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201
2023-05-01T03:30:56.439Z [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201
2023-05-01T03:30:56.439Z [INFO] core: post-unseal setup starting
2023-05-01T03:30:56.439Z [INFO] core: loaded wrapping token key
2023-05-01T03:30:56.439Z [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-05-01T03:30:56.439Z [INFO] core: successfully mounted: type=system version="v1.13.2+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-05-01T03:30:56.440Z [INFO] core: successfully mounted: type=identity version="v1.13.2+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-05-01T03:30:56.440Z [INFO] core: successfully mounted: type=cubbyhole version="v1.13.2+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-05-01T03:30:56.440Z [INFO] core: successfully mounted: type=token version="v1.13.2+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-05-01T03:30:56.441Z [INFO] rollback: starting rollback manager
2023-05-01T03:30:56.441Z [INFO] core: restoring leases
2023-05-01T03:30:56.441Z [INFO] expiration: lease restore complete
2023-05-01T03:30:56.441Z [INFO] identity: entities restored
2023-05-01T03:30:56.441Z [INFO] identity: groups restored
2023-05-01T03:30:56.441Z [INFO] core: post-unseal setup complete
2023-05-01T03:30:56.441Z [INFO] core: vault is unsealed
2023-05-01T03:30:56.443Z [INFO] core: successful mount: namespace="" path=secret/ type=kv version=""
WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variables:
$ export VAULT_ADDR='http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: qc5xNrq79dguYMUwta3wMD5GpdKX1mD6l9Astk9tSzE=
Root Token: hvs.QSsv5RT1GNZQzl8XMdK26Y5p
Development mode should NOT be used in production installations!
Welcome to Cloud Shell! Type "help" to get started.
Your Cloud Platform project in this session is set to qwiklabs-gcp-02-e8fc74852051.
Use “gcloud config set project [PROJECT_ID]” to change to a different project.
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ export VAULT_ADDR='http://127.0.0.1:8200'
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ export VAULT_TOKEN="hvs.QSsv5RT1GNZQzl8XMdK26Y5p"
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.13.2
Build Date 2023-04-25T13:02:50Z
Storage Type inmem
Cluster Name vault-cluster-7a581ccf
Cluster ID ceb6fe1f-6f63-57f6-b659-023265fae3c2
HA Enabled false
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
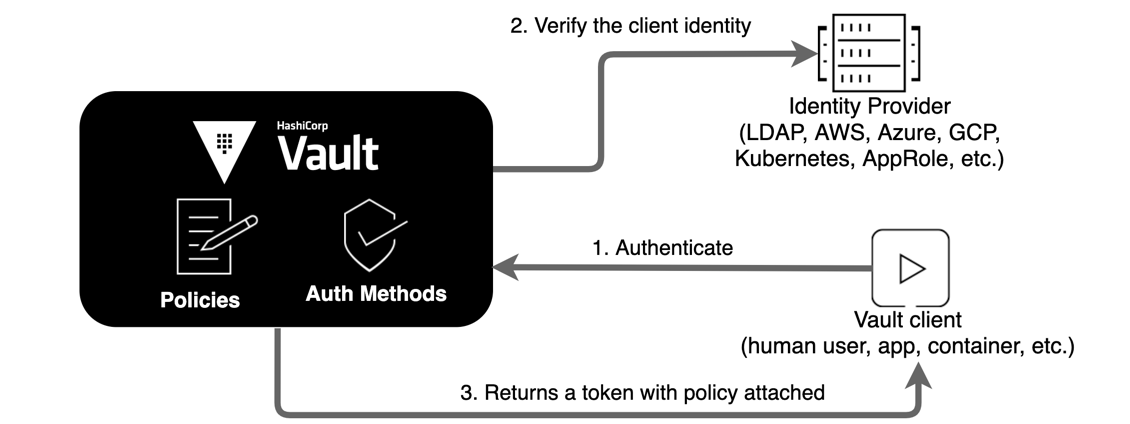
Task 3. Authentication in Vault
Before a client can interact with Vault, it must authenticate against an auth method. Upon authentication, a token is generated. This token is conceptually similar to a session ID on a website. The token may have attached policy, which is mapped at authentication time. This process is described in detail in the policies concepts documentation.
Auth methods
Vault supports a number of auth methods. Some backends are targeted toward users while others are targeted toward machines. Most authentication backends must be enabled before use. Often you will see authentications at the same path as their name, but this is not a requirement.
To learn more about authentication, you could use the built-in path-help command:
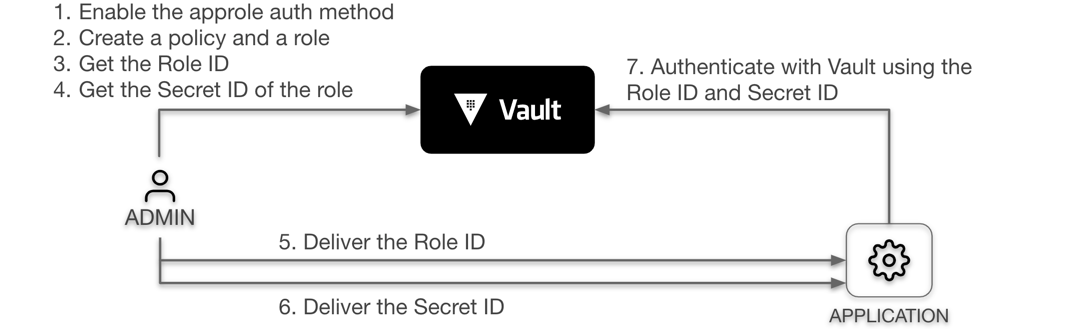
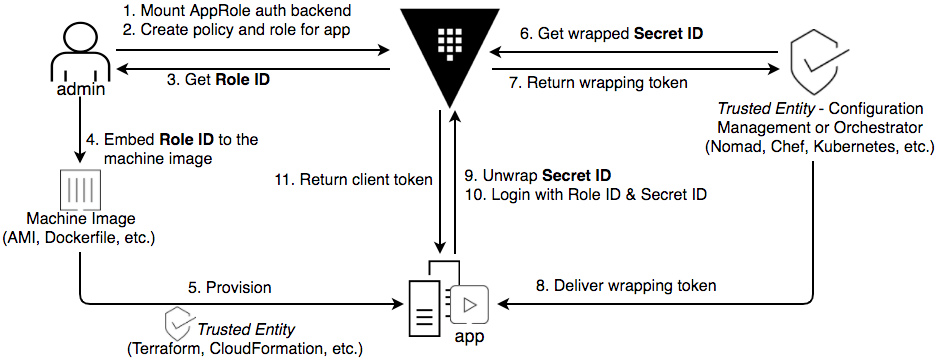
Task 4. AppRole auth method overview
The approle auth method allows machines or apps to authenticate with Vault-defined roles. The open design of AppRole enables a varied set of workflows and configurations to handle large numbers of apps. This auth method is oriented to automated workflows (machines and services), and is less useful for human operators.
An “AppRole” represents a set of Vault policies and login constraints that must be met to receive a token with those policies. The scope can be as narrow or broad as desired. An AppRole can be created for a particular machine, or even a particular user on that machine, or a service spread across machines. The credentials required for successful login depend upon the constraints set on the AppRole associated with the credentials.
Task 5. Using the AppRole auth method
Before a client can interact with Vault, it must authenticate against an auth method to acquire a token. This token has policies attached so that the behavior of the client can be governed.
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault kv put secret/mysql/webapp db_name="users" username="admin" password="passw0rd"
====== Secret Path ======
secret/data/mysql/webapp
======= Metadata =======
Key Value
--- -----
created_time 2023-05-01T03:36:37.234342043Z
custom_metadata <nil>
deletion_time n/a
destroyed false
version 1
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault auth enable approle
Success! Enabled approle auth method at: approle/
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
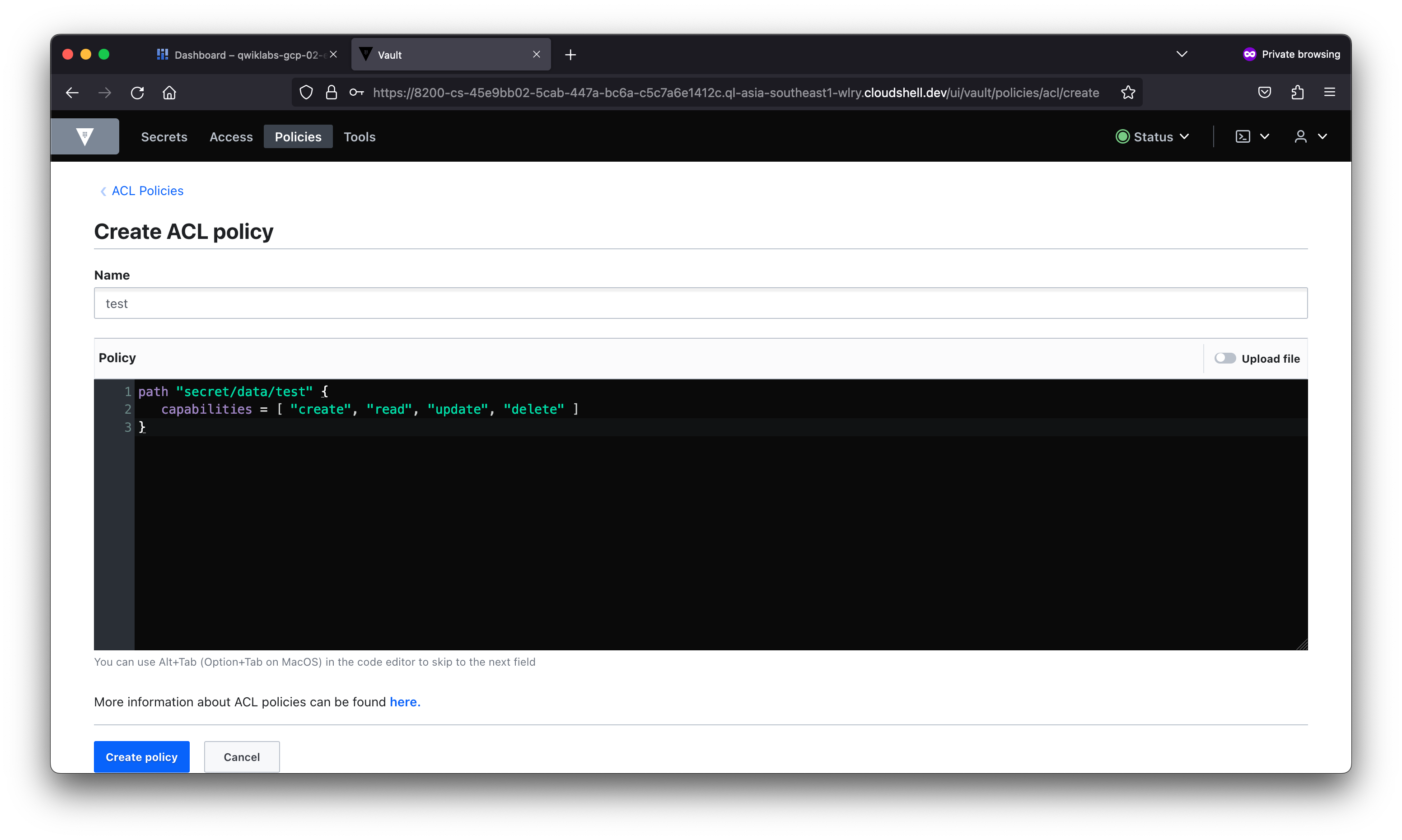
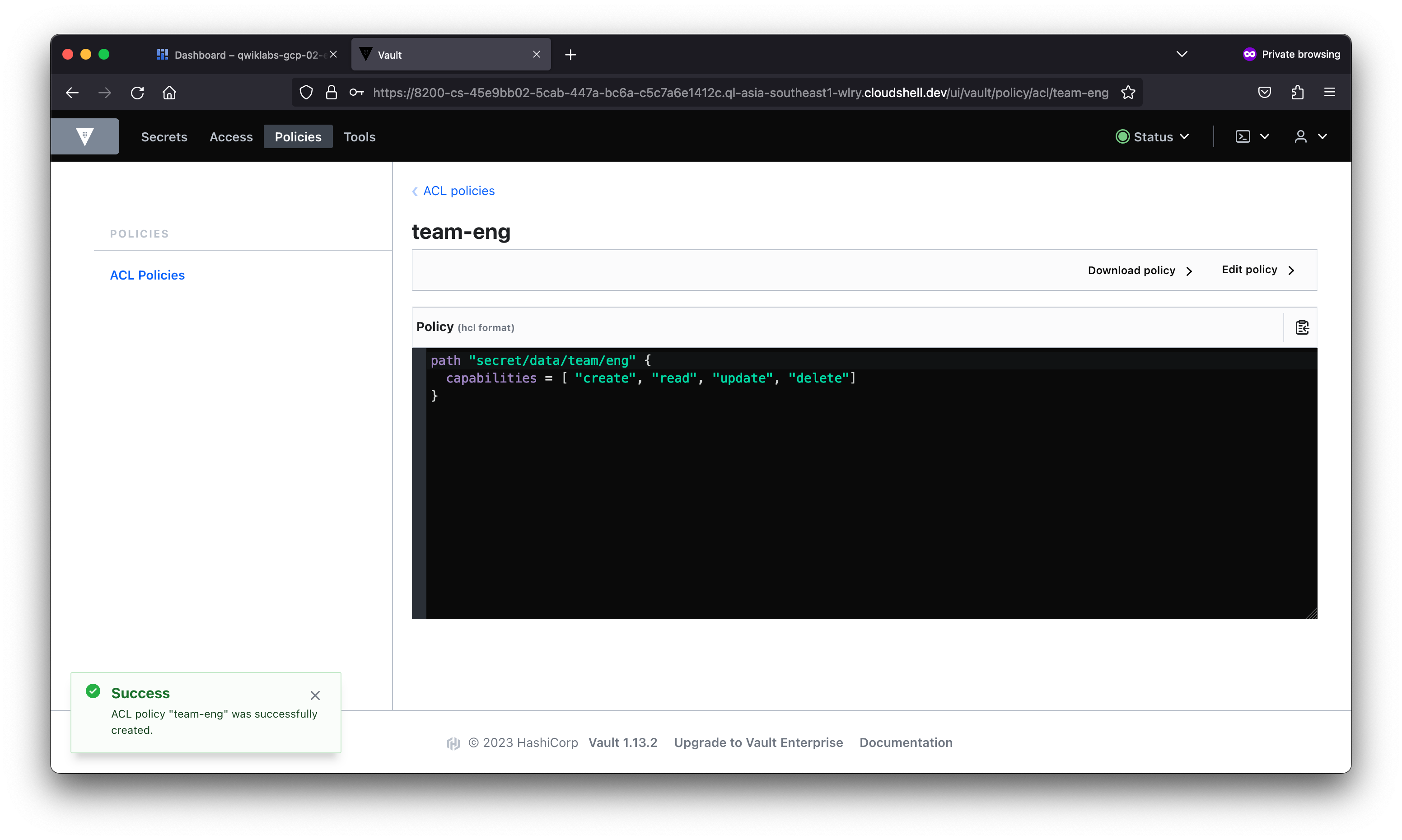
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault policy write jenkins -<<EOF
# Read-only permission on secrets stored at 'secret/data/mysql/webapp'
path "secret/data/mysql/webapp" {
capabilities = [ "read" ]
}
EOF
Success! Uploaded policy: jenkins
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
tudent_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault write auth/approle/role/jenkins token_policies="jenkins" \
token_ttl=1h token_max_ttl=4h
Success! Data written to: auth/approle/role/jenkins
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault read auth/approle/role/jenkins
Key Value
--- -----
bind_secret_id true
local_secret_ids false
secret_id_bound_cidrs <nil>
secret_id_num_uses 0
secret_id_ttl 0s
token_bound_cidrs []
token_explicit_max_ttl 0s
token_max_ttl 4h
token_no_default_policy false
token_num_uses 0
token_period 0s
token_policies [jenkins]
token_ttl 1h
token_type default
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault read auth/approle/role/jenkins/role-id
Key Value
--- -----
role_id b1100531-45d5-4377-b2b2-0ed2800cdbd0
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault write -force auth/approle/role/jenkins/secret-id
Key Value
--- -----
secret_id fd69d16f-0987-8f75-aa4d-96024042fa5e
secret_id_accessor 5986a1c5-c1c4-3562-39fe-32211ce4a046
secret_id_num_uses 0
secret_id_ttl 0s
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault write auth/approle/login role_id="b1100531-45d5-4377-b2b2-0ed2800cdbd0" secret_id="fd69d16f-0987-8f75-aa4d-96024042fa5e"
Key Value
--- -----
token hvs.CAESIG6RnEM9YgjIJGCM5KEsmLKAHAnkReYnkHauLaIL7ER6Gh4KHGh2cy5QMDk1alNNQmZNM29HR1Y3cXlBUVlKUDc
token_accessor F1kacBTUBSt10AFz21yyyBjt
token_duration 1h
token_renewable true
token_policies ["default" "jenkins"]
identity_policies []
policies ["default" "jenkins"]
token_meta_role_name jenkins
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ export APP_TOKEN="hvs.CAESIG6RnEM9YgjIJGCM5KEsmLKAHAnkReYnkHauLaIL7ER6Gh4KHGh2cy5QMDk1alNNQmZNM29HR1Y3cXlBUVlKUDc"
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ VAULT_TOKEN=$APP_TOKEN vault kv get secret/mysql/webapp
====== Secret Path ======
secret/data/mysql/webapp
======= Metadata =======
Key Value
--- -----
created_time 2023-05-01T03:36:37.234342043Z
custom_metadata <nil>
deletion_time n/a
destroyed false
version 1
====== Data ======
Key Value
--- -----
db_name users
password passw0rd
username admin
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ VAULT_TOKEN=$APP_TOKEN vault kv delete secret/mysql/webapp
Error deleting secret/data/mysql/webapp: Error making API request.
URL: DELETE http://127.0.0.1:8200/v1/secret/data/mysql/webapp
Code: 403. Errors:
* 1 error occurred:
* permission denied
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ VAULT_TOKEN=$APP_TOKEN vault kv get -format=json secret/mysql/webapp | jq -r .data.data.db_name > db_name.txt
VAULT_TOKEN=$APP_TOKEN vault kv get -format=json secret/mysql/webapp | jq -r .data.data.password > password.txt
VAULT_TOKEN=$APP_TOKEN vault kv get -format=json secret/mysql/webapp | jq -r .data.data.username > username.txt
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ export PROJECT_ID=$(gcloud config get-value project)
gsutil cp *.txt gs://$PROJECT_ID
Your active configuration is: [cloudshell-25088]
Copying file://db_name.txt [Content-Type=text/plain]...
Copying file://password.txt [Content-Type=text/plain]...
Copying file://README-cloudshell.txt [Content-Type=text/plain]...
Copying file://username.txt [Content-Type=text/plain]...
/ [4 files][ 934.0 B/ 934.0 B]
Operation completed over 4 objects/934.0 B.
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault write -wrap-ttl=60s -force auth/approle/role/jenkins/secret-id
Key Value
--- -----
wrapping_token: hvs.CAESIGuUZDy90s-sg32L8RhQ671bZMwZl5KmU9S_2y7oocTBGh4KHGh2cy5SWUx2R2MwVHBPWDZXdnlGQzRCdEpJbkE
wrapping_accessor: QjgxLTJ5epsZsmG7u94IG1Mj
wrapping_token_ttl: 1m
wrapping_token_creation_time: 2023-05-01 03:43:58.794753236 +0000 UTC
wrapping_token_creation_path: auth/approle/role/jenkins/secret-id
wrapped_accessor: fdfcb863-5a94-108b-c01a-7a10192394a7
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ VAULT_TOKEN="hvs.CAESIGuUZDy90s-sg32L8RhQ671bZMwZl5KmU9S_2y7oocTBGh4KHGh2cy5SWUx2R2MwVHBPWDZXdnlGQzRCdEpJbkE" vault unwrap
Key Value
--- -----
secret_id 9859ac70-8613-106a-9240-0e9a16c6809d
secret_id_accessor fdfcb863-5a94-108b-c01a-7a10192394a7
secret_id_num_uses 0
secret_id_ttl 0s
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault write auth/approle/role/jenkins token_policies="jenkins" \
token_ttl=1h token_max_ttl=4h \
secret_id_num_uses=10
Success! Data written to: auth/approle/role/jenkins
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault login -method=userpass -path=userpass-test \
username=bob password=training
WARNING! The VAULT_TOKEN environment variable is set! The value of this
variable will take precedence; if this is unwanted please unset VAULT_TOKEN or
update its value accordingly.
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token hvs.CAESIBNWq9zLXV4qcqKIV_RyOrWMJF9pelpWQboFJOhnOrHbGh4KHGh2cy5LR2RtZnJuYW9tVU5mYVdrUkYxTTFHTkQ
token_accessor XEdoh8KkDd8QMv16s9xPEBoJ
token_duration 768h
token_renewable true
token_policies ["default" "test"]
identity_policies ["base"]
policies ["base" "default" "test"]
token_meta_username bob
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault token capabilities hvs.CAESIBNWq9zLXV4qcqKIV_RyOrWMJF9pelpWQboFJOhnOrHbGh4KHGh2cy5LR2RtZnJuYW9tVU5mYVdrUkYxTTFHTkQ secret/data/training_test
create, read
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
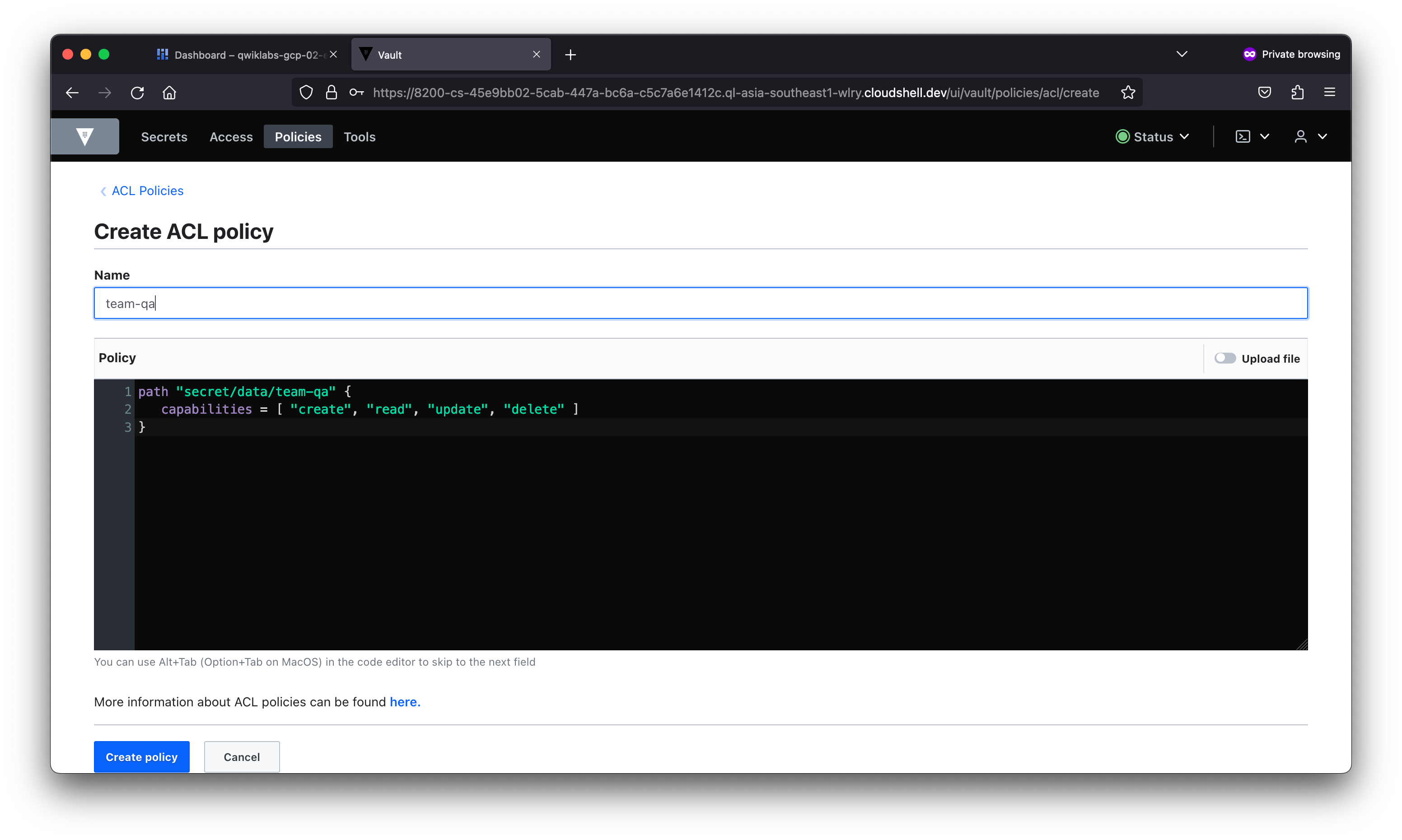
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault token capabilities hvs.CAESIBNWq9zLXV4qcqKIV_RyOrWMJF9pelpWQboFJOhnOrHbGh4KHGh2cy5LR2RtZnJuYW9tVU5mYVdrUkYxTTFHTkQ secret/data/team-qa
deny
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
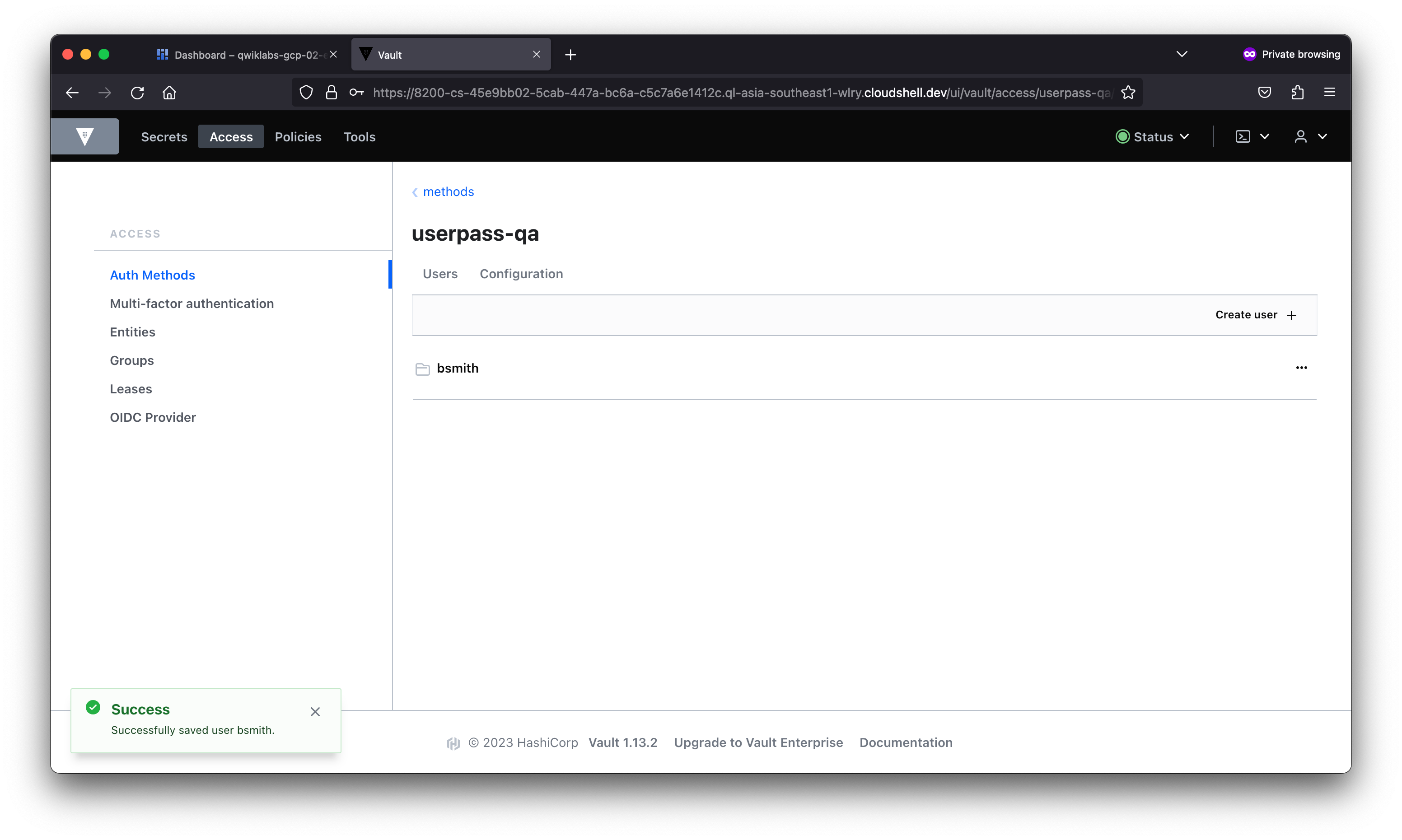
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault login -method=userpass -path=userpass-qa \
username=bsmith password=training
WARNING! The VAULT_TOKEN environment variable is set! The value of this
variable will take precedence; if this is unwanted please unset VAULT_TOKEN or
update its value accordingly.
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token hvs.CAESIPvlbvUhIMF2WtuFslLXlLokDK-w37MTSyokeRkXLgKKGh4KHGh2cy5hMUs4aVJMTVJxNE5PU05uNW45MHRpWGM
token_accessor 5EqWRTuemzwpnot67yQpgRNX
token_duration 768h
token_renewable true
token_policies ["default" "team-qa"]
identity_policies ["base"]
policies ["base" "default" "team-qa"]
token_meta_username bsmith
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
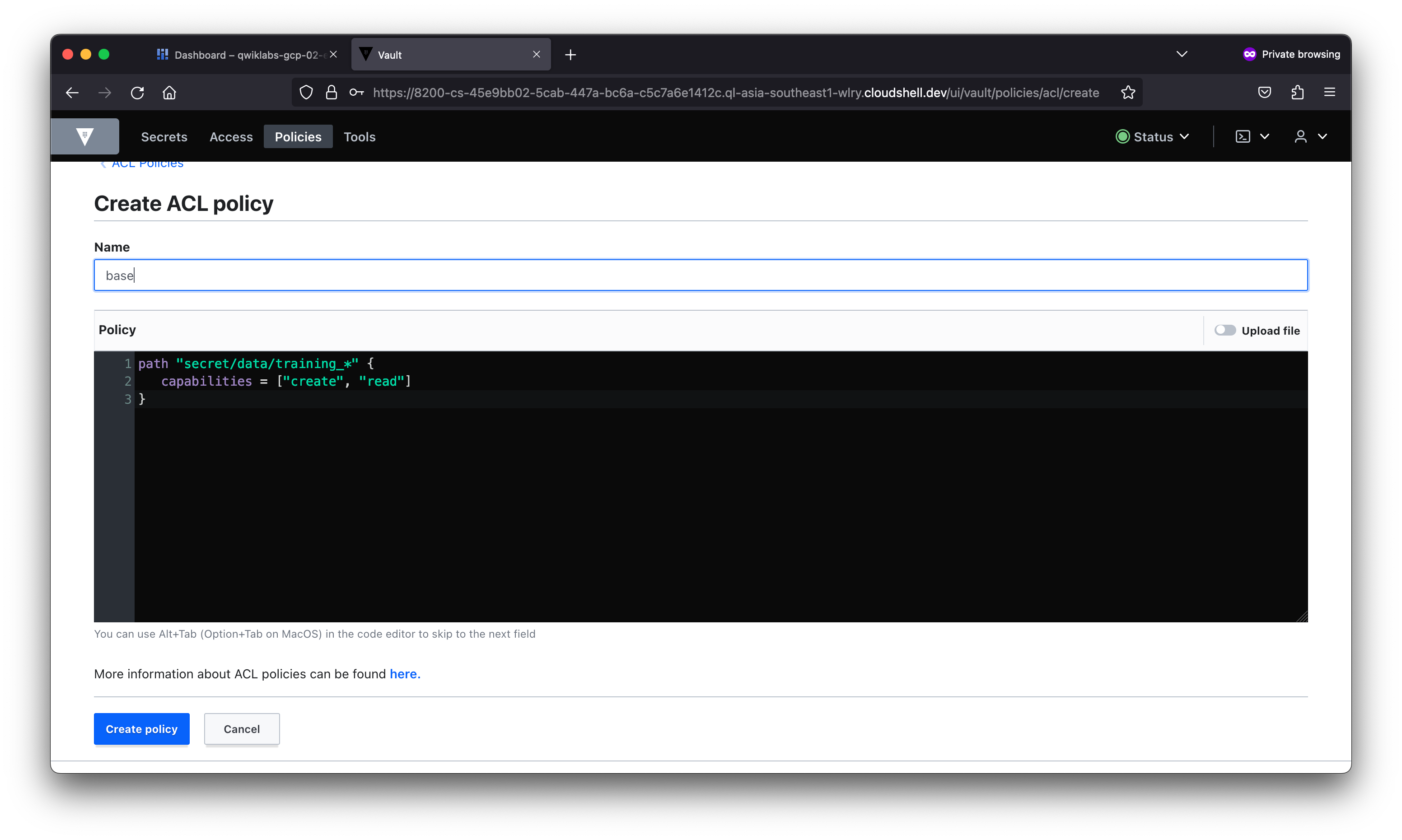
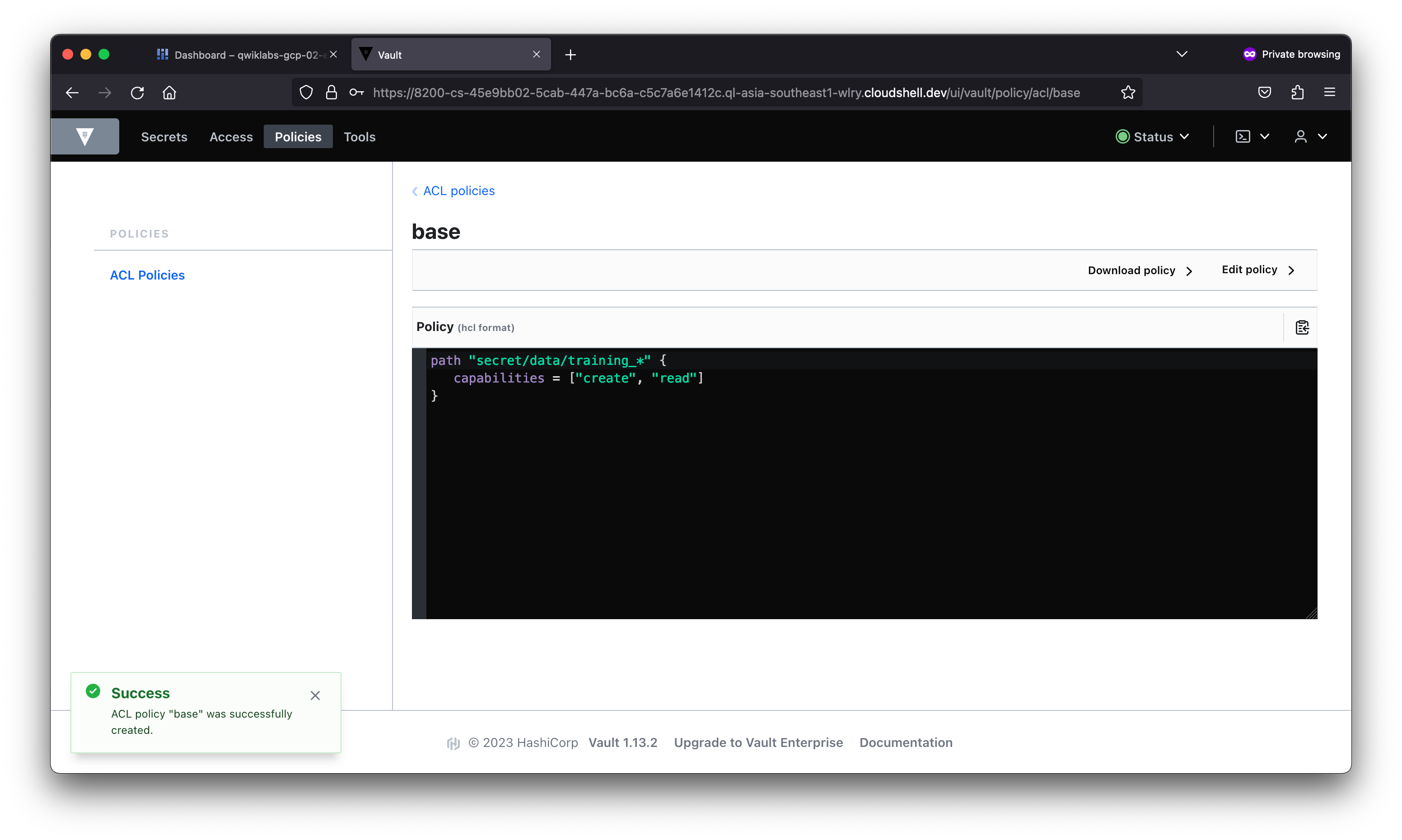
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$ vault login -method=userpass -path=userpass-test username=bob password=training
WARNING! The VAULT_TOKEN environment variable is set! The value of this
variable will take precedence; if this is unwanted please unset VAULT_TOKEN or
update its value accordingly.
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token hvs.CAESIJomNjVSxvhc0w3YN7ek_efcQsynfGzyAk72FOlLcEUrGh4KHGh2cy55NXVhRmNGcUZEcmVOS2o0QzBYVDZndHY
token_accessor Vgle2QnZo9yrTsk87c2tqxcP
token_duration 768h
token_renewable true
token_policies ["default" "test"]
identity_policies ["base" "team-eng"]
policies ["base" "default" "team-eng" "test"]
token_meta_username bob
student_02_a5be9b1b005d@cloudshell:~ (qwiklabs-gcp-02-e8fc74852051)$
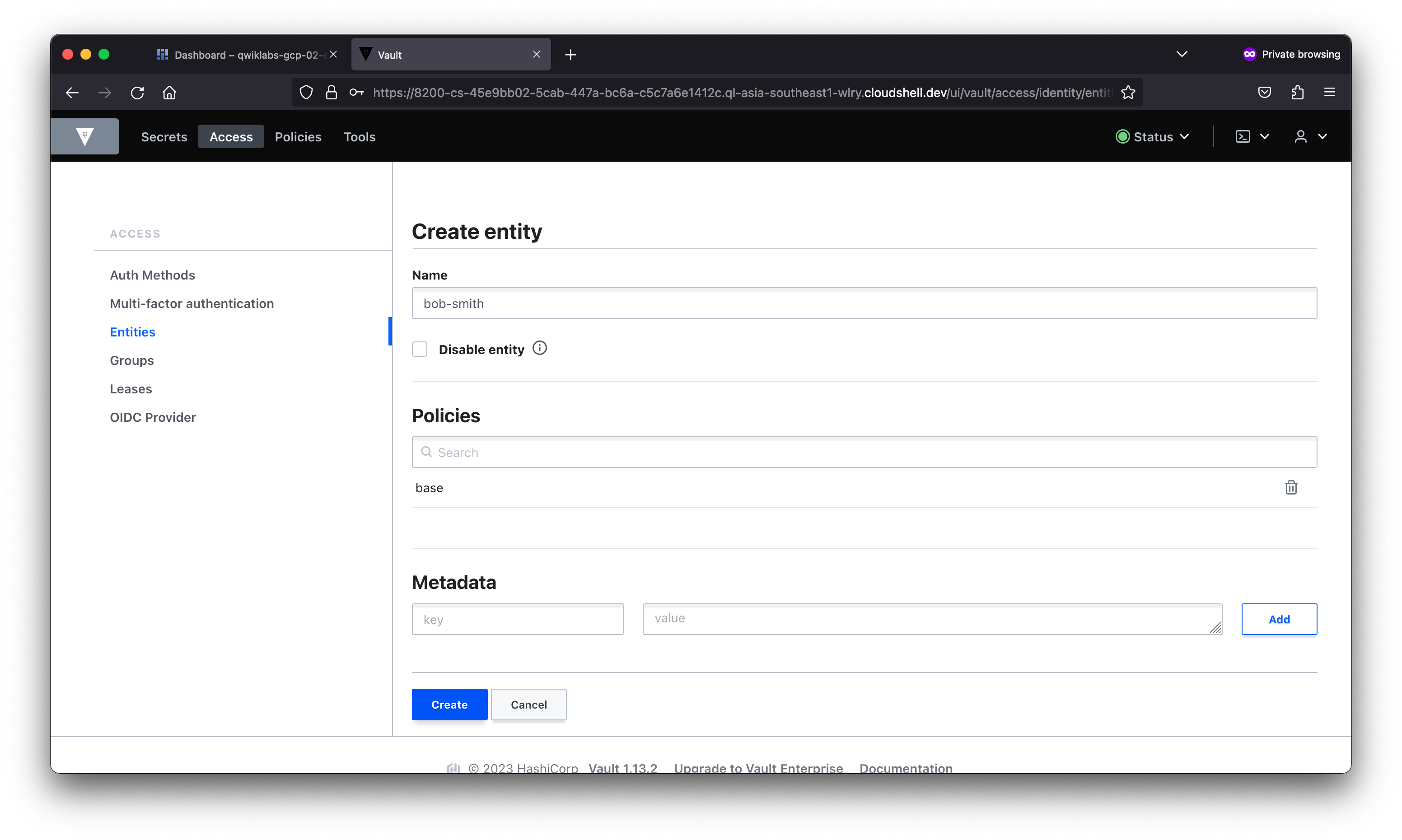
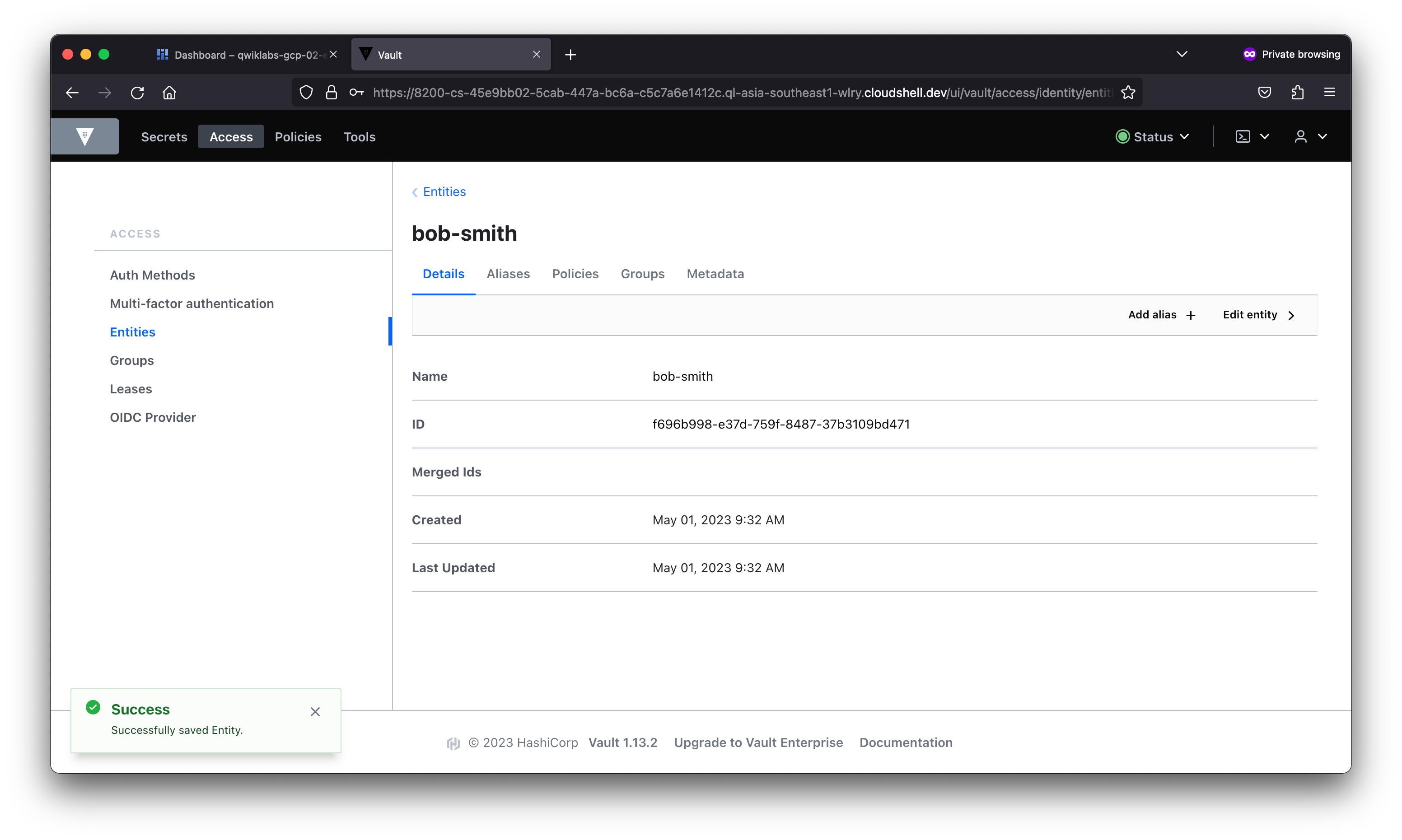
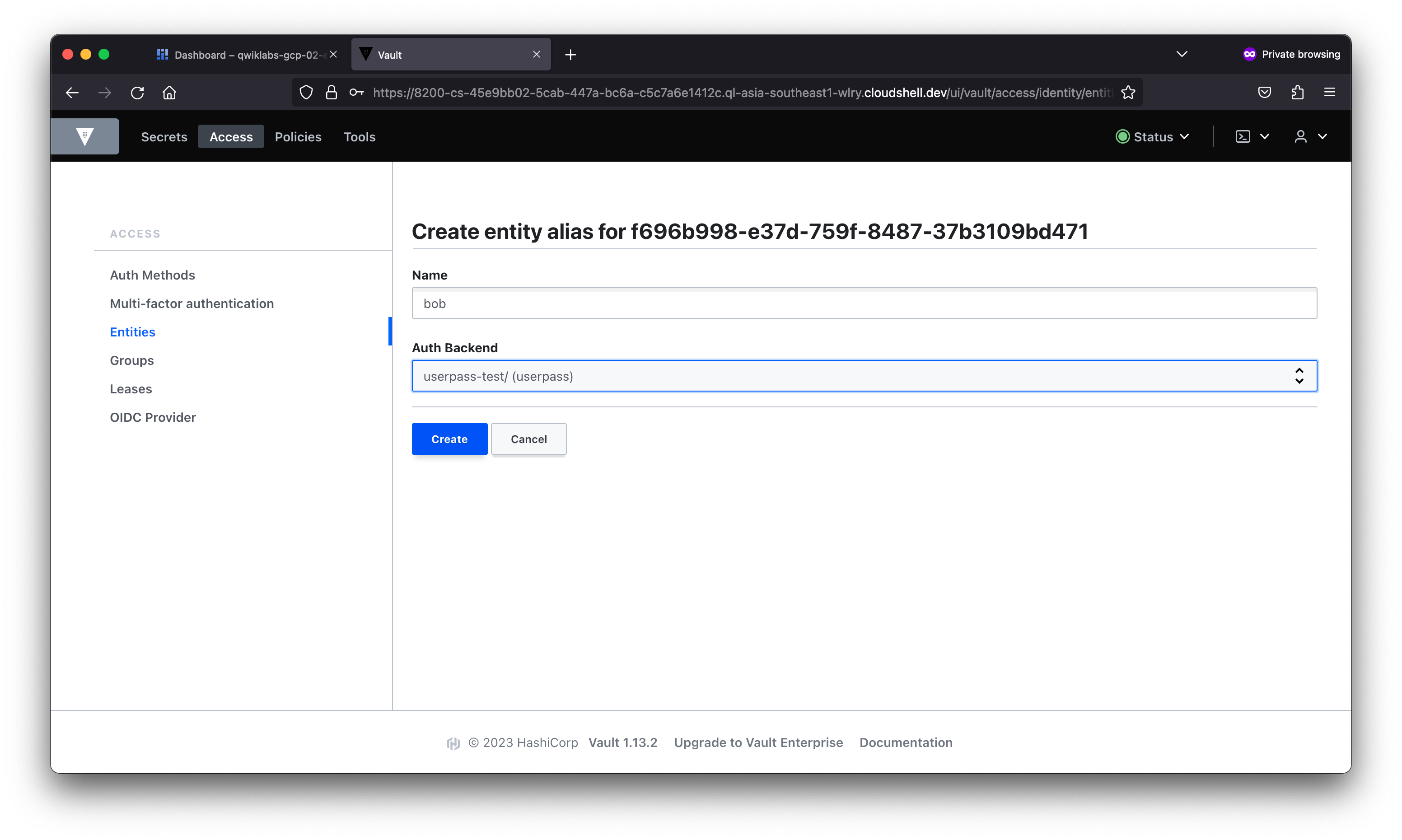
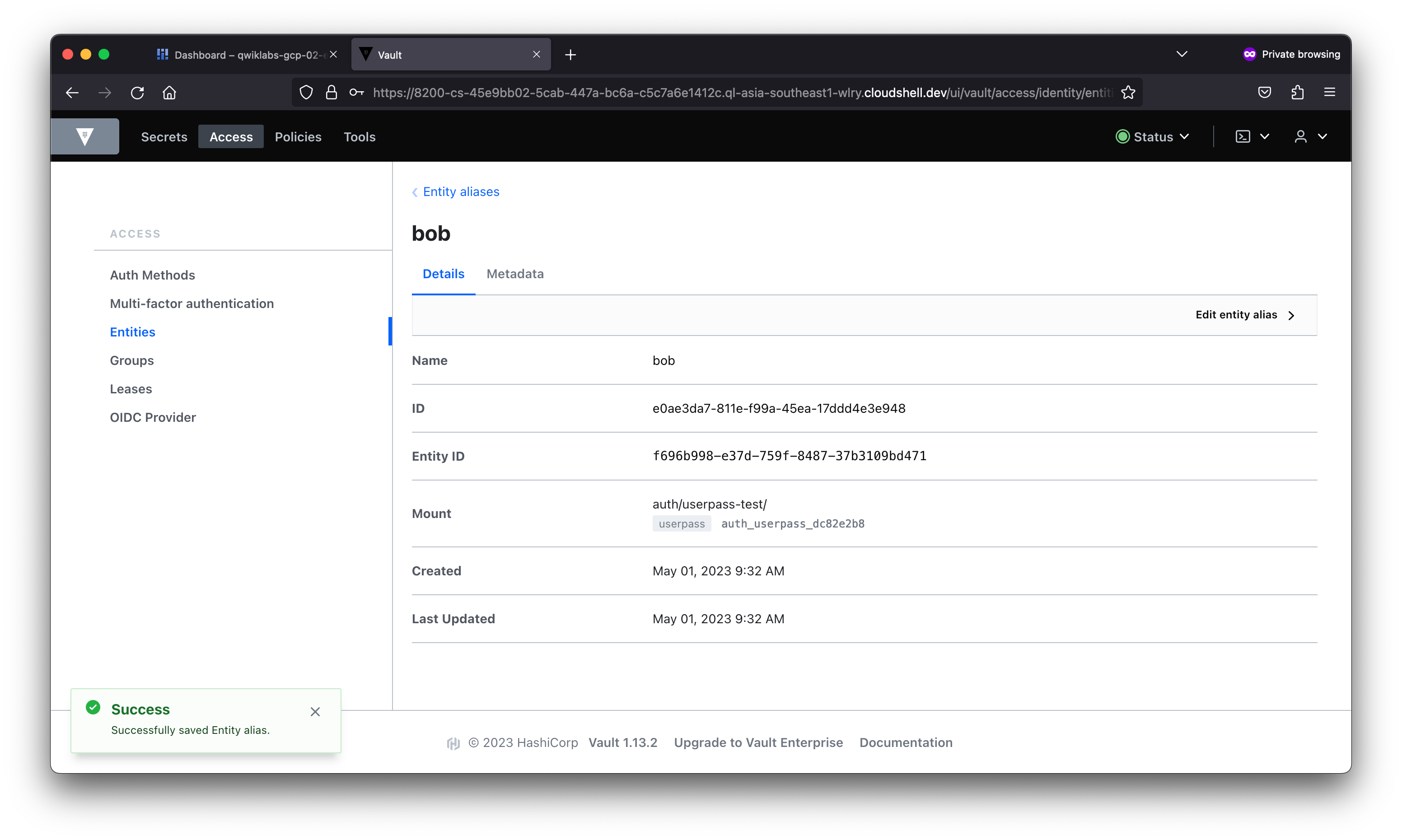
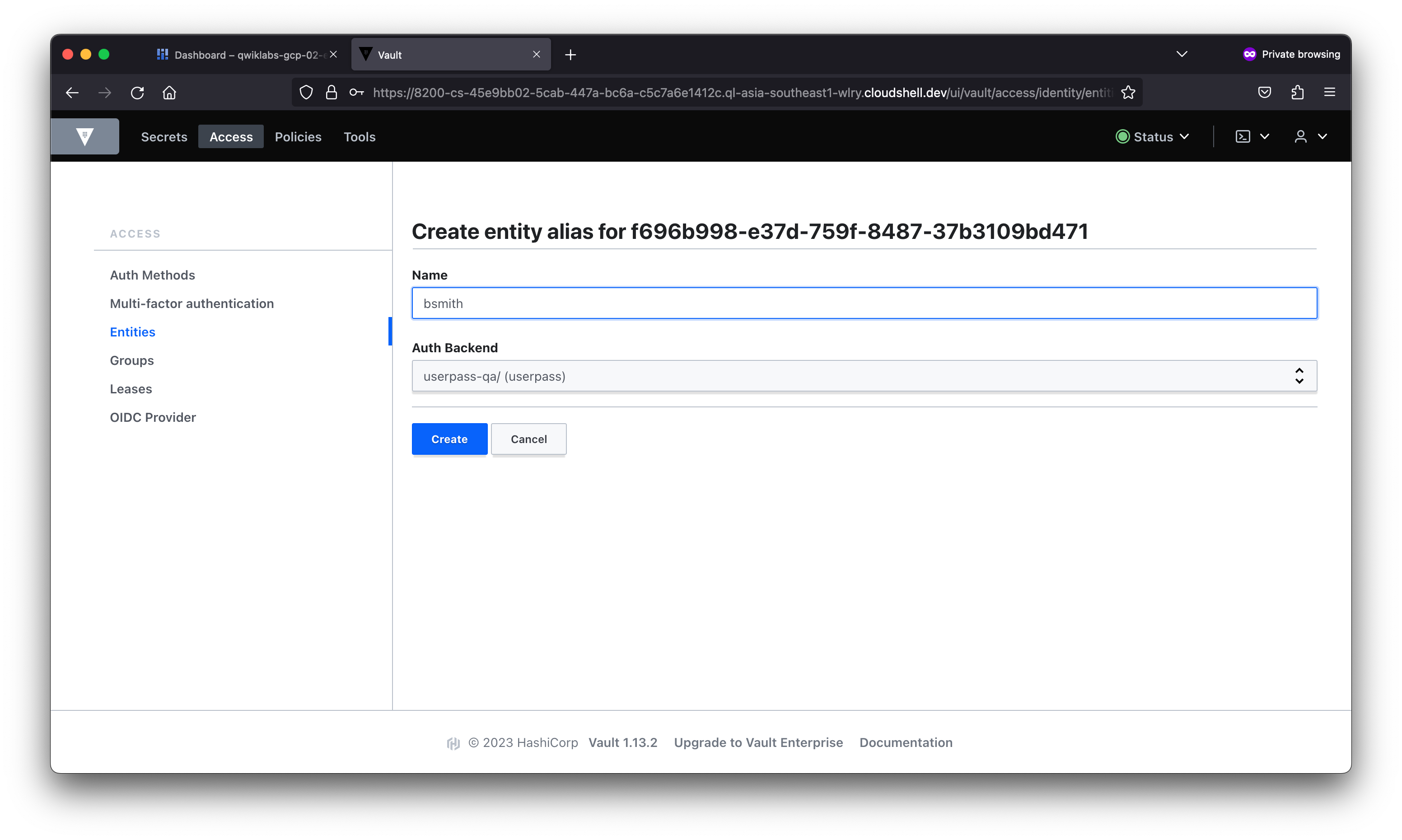
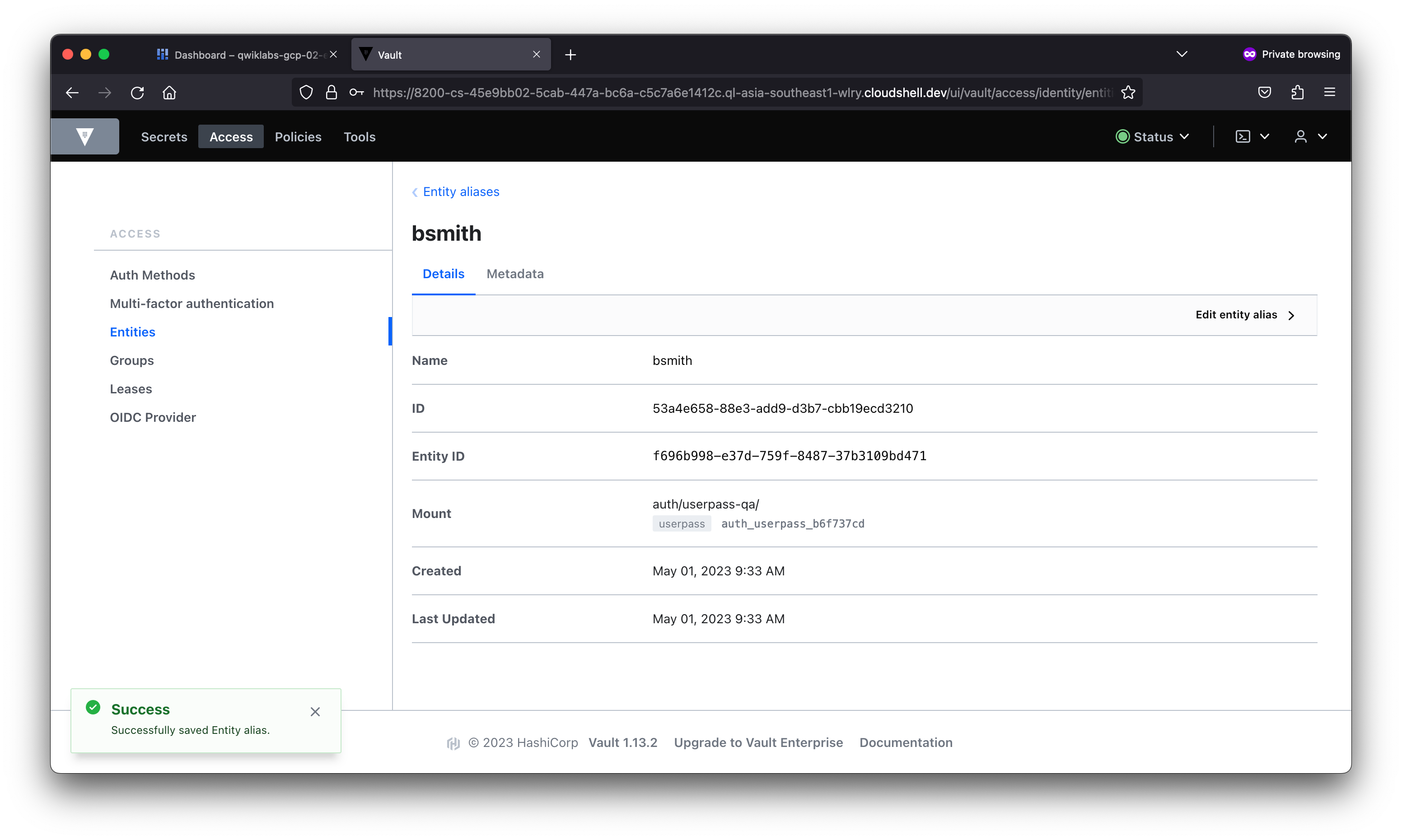
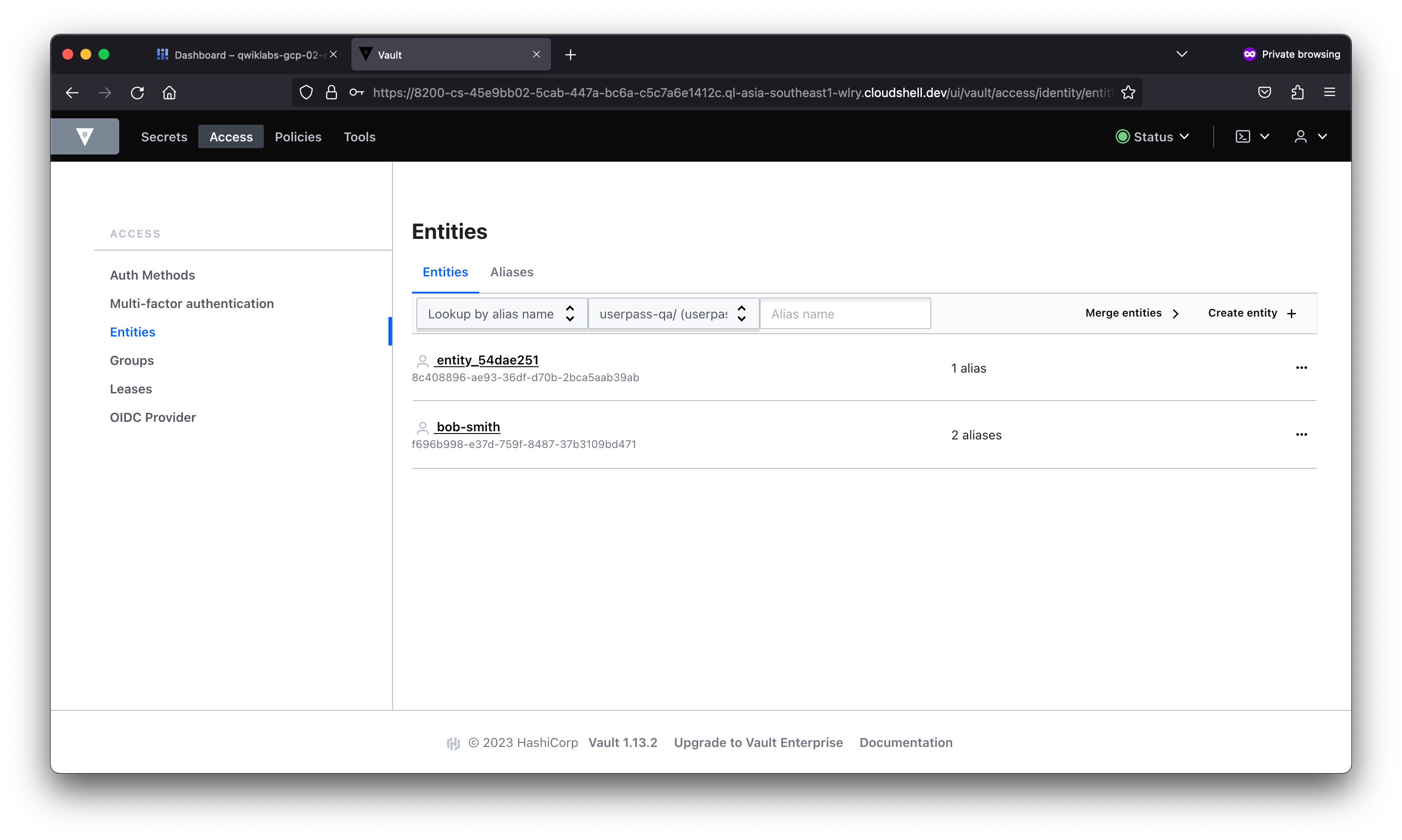
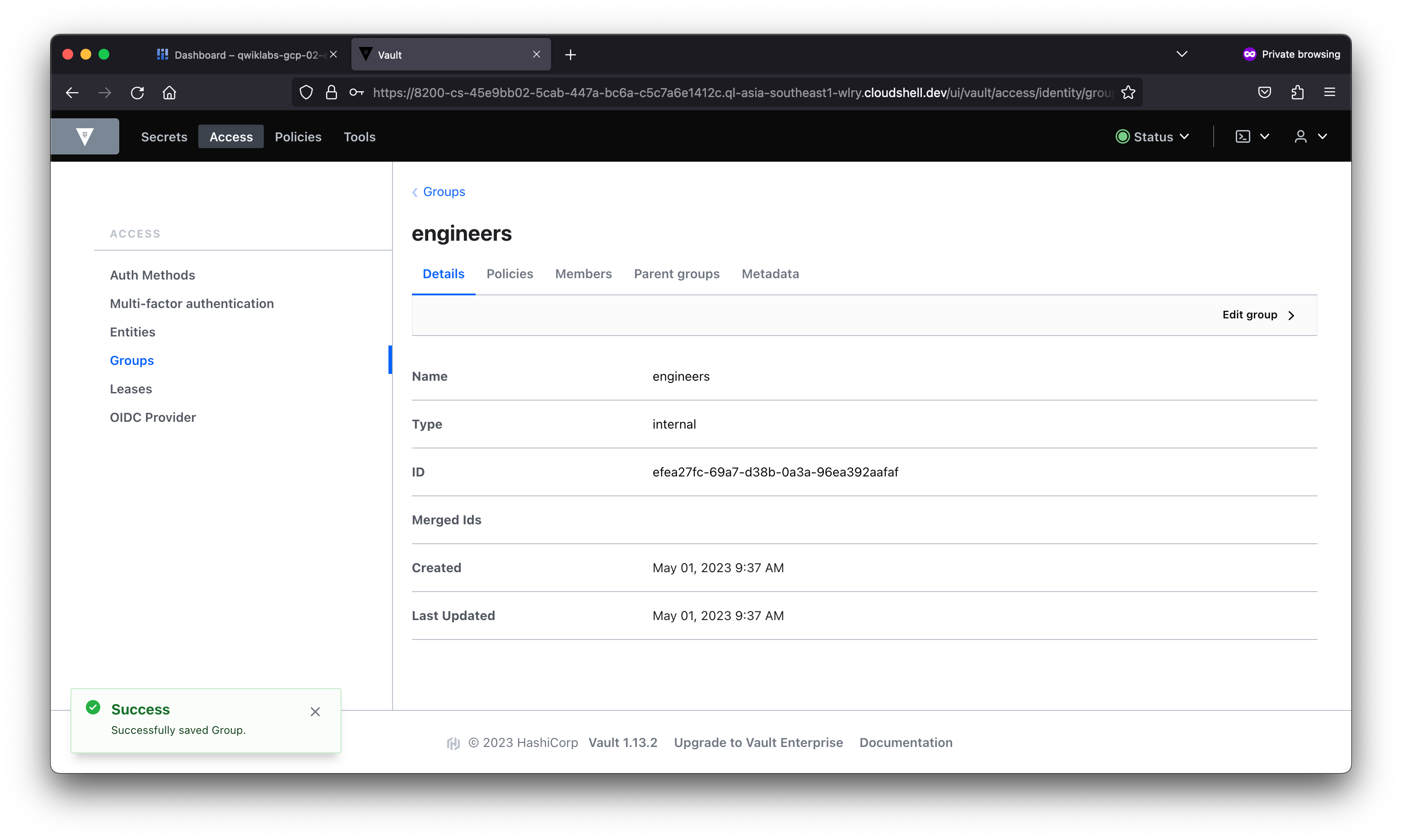
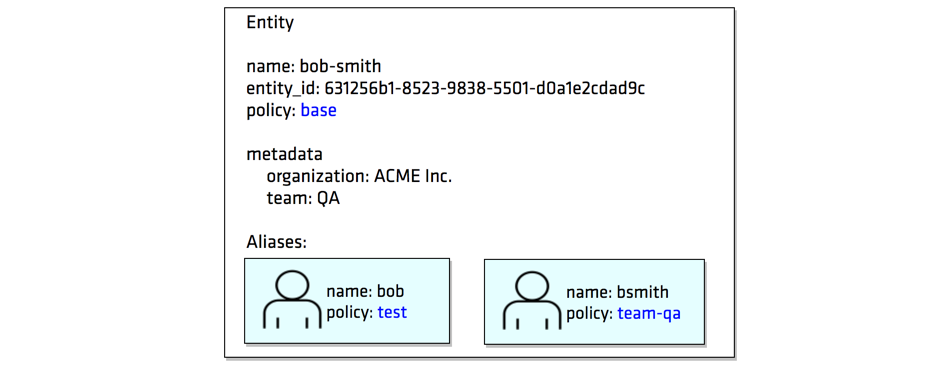
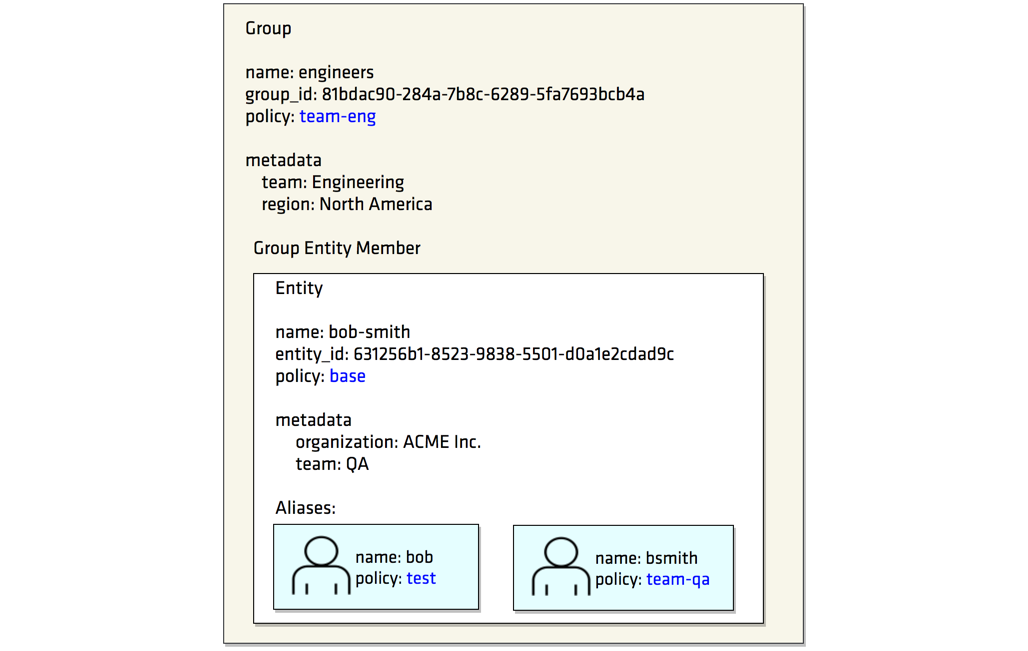
In this lab, you learned about the different types of authentication and used the AppRole auth method in Vault. You then created users with distinct policies, associated aliases as entity members to an entity with a base policy, and created an internal group with an entity member.